Defensics® Fuzzing is a comprehensive, versatile, automated black box fuzzer that enables organizations to efficiently and effectively discover and remediate security weaknesses in software.
A comprehensive fuzzing framework
- The generational fuzzer takes an intelligent, targeted approach to negative testing.
- Advanced file and protocol template fuzzers enable users to build their own test cases.
Fuzz testing is experiencing a resurgence
The number of years fuzzing has been a proven security and quality testing technique
The number of connected devices expected to be used by 2025
Learn more about Defensics
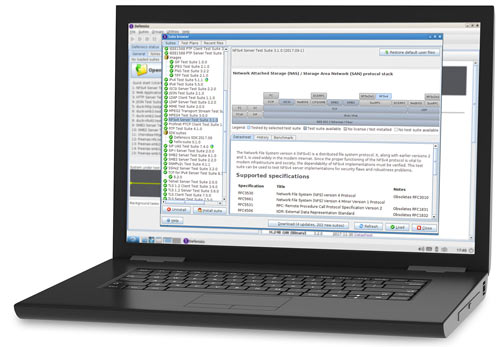
Fuzz testing smarter with the Defensics platform
Defensics is a comprehensive, flexible fuzzing tool that enables users of all proficiency levels to employ this powerful security testing technique.
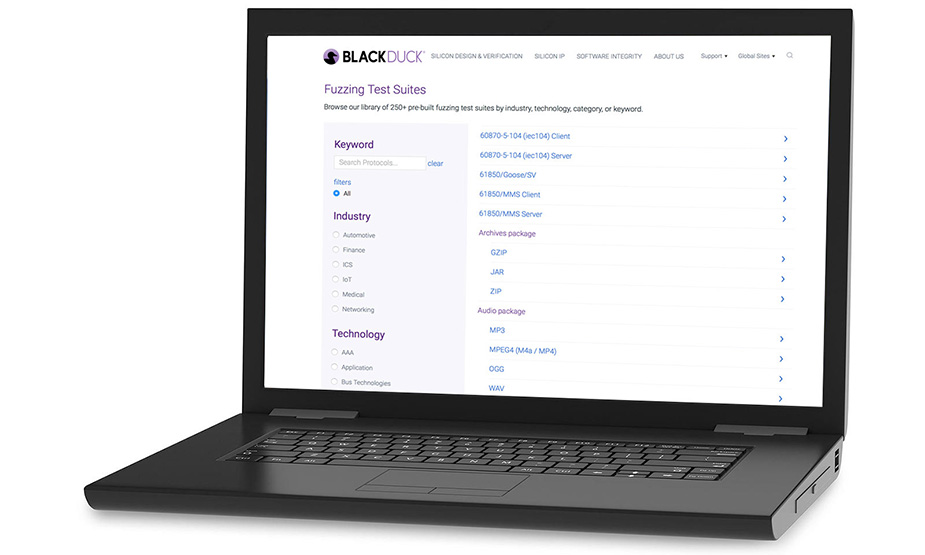
Test faster with Defensics test suites
Browse the Defensics library of 300+ prebuilt fuzz testing suites, which are continuously maintained by our team of engineers to include more RFCs, more specifications, and more protocols, file formats, and interfaces.

Fits into most development life cycles
Defensics contains workflows that enable it to fit almost any environment. Whether you employ a traditional SDL or a CI development life cycle, we fit into your development process early, enabling you to catch and remediate vulnerabilities in a more cost-effective manner.
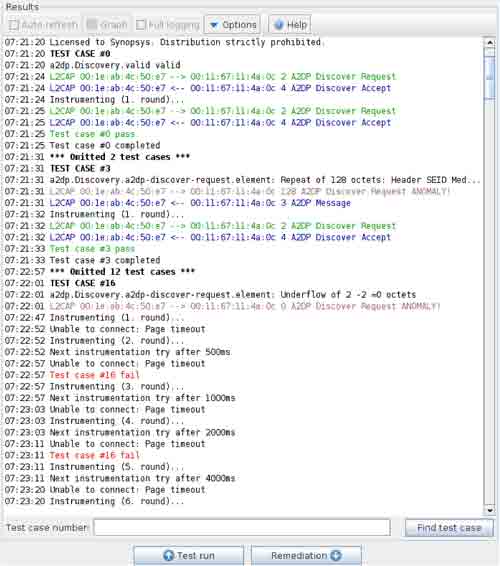
Detailed, data-rich reports for efficient remediation
Our comprehensive reports include contextualized logs that detail the protocol path and message sequences, vulnerability mapping to industry standards such as CWE and injection type, and single test cases so you can re-create each issue and verify the fix. You can also generate remediation packages for your suppliers to facilitate secure, collaborative remediation across the supply chain.
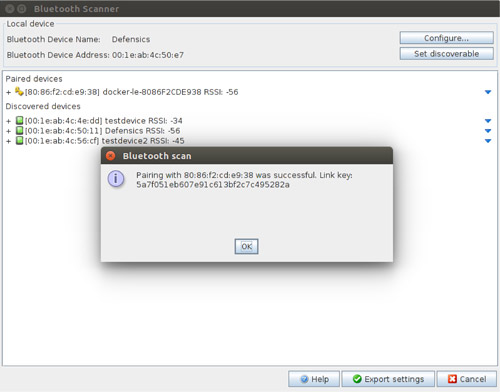
Scale fuzz testing with automation
From scanning for the test target to determining the number of layers to connect to, Defensics offers a rich set of APIs for flexible, scalable automation to meet all your needs.
A versatile fuzzer that fits any team’s needs
Procurement
Development
Quality assurance
Security
Properly executed fuzzing techniques can provide a low-cost, efficient means of finding vulnerabilities, covering more code paths and value iterations than a manual analysis can perform in a short period of time.”
Uncover more about fuzzing
Securing 5G and IoT with Fuzzing
Commonly asked questions on fuzz testing
Get RFC specification coverage, test tool features, and tool-specific information for our 300+ test suites.
What is fuzzing?
5G: Vast potential, but better security needed
Improving Fuzz Testing of Infotainment Systems and Telematics Units