Subscribe
Cybersecurity in medical devices has become a hot topic for both medical and IoT verticals, and it is starting to gain government attention, too. Last year, the Food and Drug Administration (FDA) released the “Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions” standard, which calls for medical device manufacturers to use fuzz testing during the software development life cycle to identify and address potential security issues.
What is fuzz testing
Fuzz testing is an automated software/protocol testing technique that involves feeding random or invalid data inputs to a target to discover vulnerabilities, crashes, or other unexpected behavior. It aims to uncover software flaws and security vulnerabilities that might not be easily detected through traditional testing methods. Inputs can be malformed, mutated, or randomly generated data that deviates from the expected input structure—the fuzzer then uses instrumentation to observe the program's responses, looking for abnormalities such as crashes, hangs, memory leaks, or incorrect output.
Instrumentation in fuzz testing refers to the process of monitoring the target software or system under test to collect additional information during the fuzzing process. It can be as simple as using a known good communication “ping” to see if the target is still in a healthy state or as complicated as monitoring the code with an agent or debugger hooked up to the target device (see Figure 1).
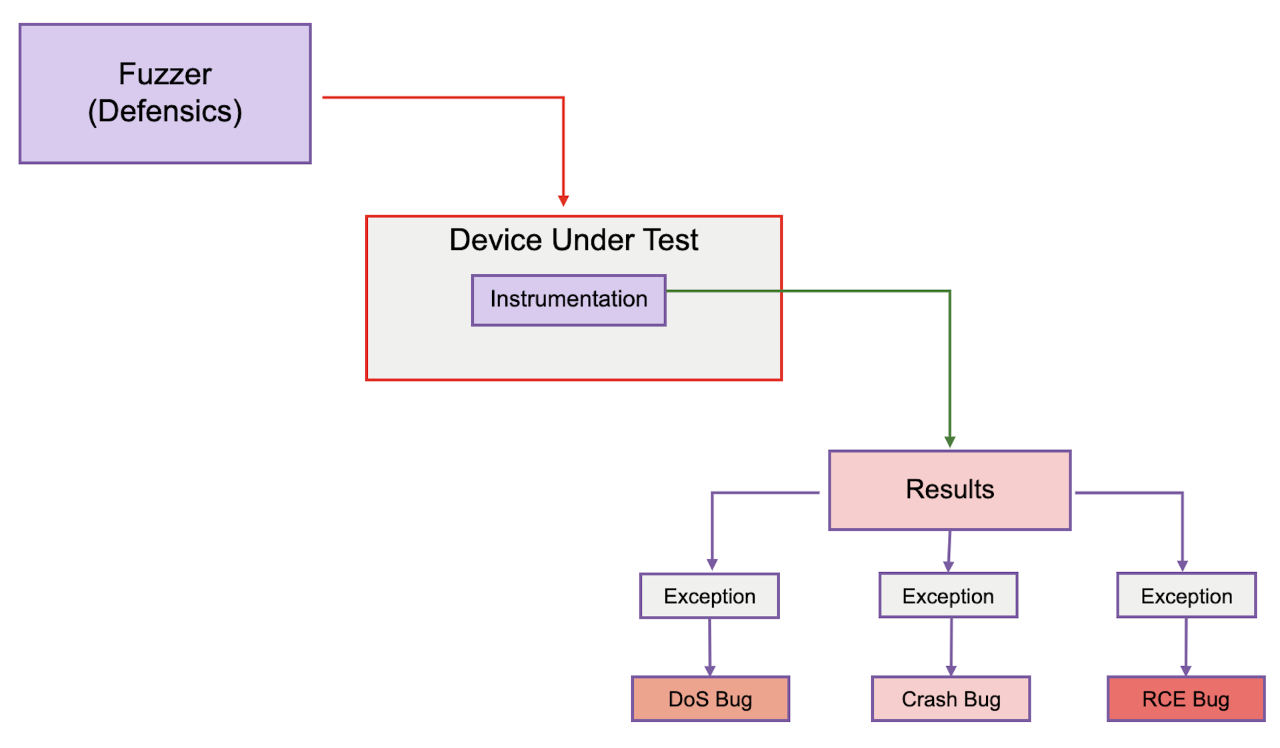
Firgure 1. Fuzz testing.
How to comply with the new fuzzing standard
To comply with the new guidance, device manufacturers will need to add a fuzz testing solution to their risk management plans as a testing procedure. Successfully adding such a program will mean following these steps:
- Identify the attack surface. Document all the potential entry points that attackers could exploit to compromise the security of your devices. This includes analyzing software and firmware components, communication protocols, and any other potential attack vectors.
- Select appropriate fuzz testing tools and techniques. Choose the fuzz testing tools and techniques that best suit your device and its software/firmware components. Be sure to look at both the commercial and open source tools available in the market.
- Develop test cases. Create a set of comprehensive, diverse, and repeatable test cases that cover a wide range of inputs, including both expected and unexpected data. These test cases should aim to simulate various attack scenarios and potential vulnerabilities.
- Execute fuzz testing. Conduct fuzz testing and monitor the device's behavior during the test via instrumentation. Communication pings ensure that the device hasn’t crashed when testing,
- Analyze results. Carefully review the results of the fuzz testing to identify any vulnerabilities or security weaknesses that have been uncovered. Prioritize the identified issues based on their severity and potential impact.
- Address identified vulnerabilities. Develop a plan to address and remediate the identified vulnerabilities. This may involve implementing patches, updates, or changes to the device's software/firmware. Follow established best practices for vulnerability management and ensure that appropriate security controls are implemented.
- Document the fuzz testing process. Log the fuzz testing process you followed, including the tools used, test cases executed, results obtained, and actions taken to address identified vulnerabilities. This documentation will serve as evidence of compliance during regulatory audits or inspections.
Vulnerabilities that fuzzing can catch
The new FDA standard offers the medical device field a chance to catch up with and address some of the vulnerabilities that fuzzing has found in other systems.
In 2019, for example, a new cybersecurity vulnerability called Urgent11 was discovered in a real-time operating system called VxWorks, which is widely used in embedded devices, including medical equipment, industrial control systems, and IoT devices. Urgent11 vulnerabilities are significant because they allow remote attackers to gain unauthorized access to vulnerable devices and potentially execute arbitrary code or launch malicious attacks. The flaws stem from a TCP/IP networking stack that is part of VxWorks and affect versions 6.5 and prior.
These types of vulnerabilities can be exploited by sending specially crafted packets to the targeted device, triggering a buffer overflow or other memory corruption issues. Once exploited, an attacker can potentially take control of the affected device, leading to severe consequences such as remote code execution, data theft, system disruption, or even compromised connected networks. The use of fuzz testing on significant software releases could help eliminate certain vulnerabilities that are hard to catch and prevent zero-day vulnerabilities. Urgent11 has raised awareness about the importance of timely security updates, vulnerability management, and risk assessment in the context of IoT and embedded devices.
Conclusion
The introduction of new guidance by the FDA emphasizing the use of fuzz testing in medical devices highlights the growing importance of cybersecurity in IoT and medical spaces. The implementation of fuzz testing and adherence to the new standard can significantly enhance the cybersecurity posture of medical devices. By proactively identifying and mitigating vulnerabilities, manufacturers can minimize the risk of unauthorized access, data breaches, system disruptions, and other potential threats.








